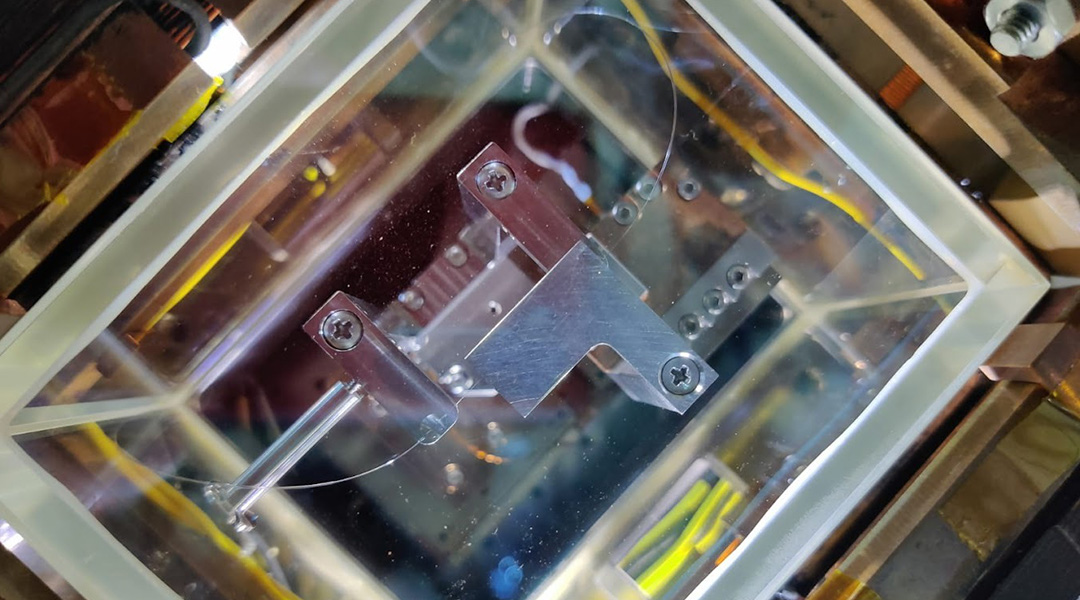
Interest in quantum technologies, particularly quantum communications, is growing as it seeks to improve data security, which is increasingly becoming compromised in the modern world.
The demand arises from the assumption that communication via quantum technology is theoretically impossible to hack, but it’s suspected that in practice it may not be completely secure.
To figure this out, researchers probed one of the most actively studied types of quantum cryptography called quantum key distribution. They wanted to find out if an eavesdropper could in fact tamper with a key transfer, obtain information about it, and whether such tampering would go undetected by the communicating parties.
“Using [the quantum key distribution] method, remote parties can utilize judicious measurements performed on quantum states of light to generate a secret key that only they know and then use it to encrypt and decrypt their communication,” said Ariel Ashkenazy, a Ph.D. student at Bar-Ilan University and one of the authors of the study, in an email.
“The security of these protocols is based upon the principles of quantum mechanics, which is one of the best theories we have to describe nature.”
Using photons to encode information
The most secure way of implementing quantum key distribution often considered in theoretical studies is by encoding the key in the states of single photons being transmitted between the communicating parties.
In this setup, security is ensured by a fundamental law of quantum mechanics that measuring the state of a quantum system inevitably alters it, which makes any attempt by an eavesdropper to intercept and measure a photon detectable by a receiving party.
However, single photon sources are currently complex, expensive, and provide low data transfer rates. Consequently, the key is often transmitted using laser pulses which may consist of more than one photon, which potentially makes the protocol vulnerable.
“On the theoretical level, it has been known for years that practical implementations of quantum key distribution are vulnerable to the so-called ‘photon-number splitting’ attack,” said Yuval Idan, another of the study’s scientists. “Using this attack, the eavesdropper, Eve, who tries to infer the secret key generated by two parties, Alice and Bob, can intercept the pulses of light sent by Alice, decide whether they contain more than one photon and in these cases take a portion of the pulse and measure it to gain valuable information.
“However, it was believed to be beyond the capabilities of current technologies, with some researchers deeming the attack ‘unrealistic’. In light of the above, the main finding of our study is the proposal of a possible implementation of photon-number splitting attack utilizing current experimental capabilities.”
Implementing a photon-splitting attack
In their study published in Advanced Quantum Technologies, the scientists explored a specific implementation of a photon splitting attack, in which an eavesdropper uses a method called single-photon Raman interaction (SPRINT) to split off a single photon from the beam.
“To succeed in the [attack], a remarkable level of control, of both light and matter, is needed,” said Eliahu Cohen. “We propose a proven capability of making a single photon interact with a single properly controlled atom. This [Raman] interaction results in reflection of a single photon from the pulse [to the receiving party], while the reflecting atom then becomes “transparent” to subsequent photons in the pulse [transmitted to the eavesdropper].”
By applying the rules of quantum physics to the photon-atom interaction, the researchers calculated the amount of information about the key that an eavesdropper could extract from all but one photon from the beam, and an error rate that such an interaction introduces into the signal that the receiving party gets.
They found that if the number of photons in each laser pulse is large, an eavesdropper can obtain substantial information (though not all) about the transferred key while introducing only a small error in the data obtained by the receiving party. This finding suggests that quantum key distribution using multi-photon pulses is vulnerable to photon-splitting attacks, contrary to the idealized setup often studied in theoretical works.
“Our results show that an almost ideal photon-splitting attack is well within the capabilities of contemporary technologies,” said Ashkenazy. “However, that is not to say that quantum key distribution is doomed, as there are several ways to defend against such attack either by using more advanced quantum key distribution protocols [consisting in different methods of encoding and decrypting information], or by utilizing advanced technologies such as photon-number-resolving detectors [allowing detection of the disappearance of photons from laser beams].”
“Our analysis shows, on the one hand, the inherent challenges of quantum information retrieval — even with a novel, dedicated PNS setup, there’s still disturbance to multiple-photon states,” added Cohen. “On the other hand, it shows the necessity of various countermeasures, such as decoy states, which enable the growing use of quantum key distribution to be secure.”
“Rather, from the perspective of the communicating parties, our results underscore the importance of adopting these countermeasures against photon-number splitting attacks to uphold the security of quantum key distribution systems,” continued Ashkenazy. “From the point of view of an aspiring eavesdropper, our results encourage the experimental implementation of such a SPRINT-based attack.”
Despite the depth and detail of the theoretical analysis carried out by the authors, the photon-number splitting attack based on the SPRINT method is only one of many eavesdropping options. To verify the validity of their conclusion for the method as a whole, further experimental and theoretical studies of hacking secure quantum communications are necessary.
“The lab of Barak Dayan [one of the current study’s authors] at the Weizmann Institute of Science is now performing an experiment for supporting the theoretical analysis,” said Ashkenazy. “We believe these results are inherent to the photon-number splitting attack.
“However, since our analysis only investigates a specific implementation of the attack, we can not use it as a proof for this claim. Thus, further investigation is needed of the effect of the photon splitting attack on the carried information.”
Reference: Eliahu Cohen, et al., Photon Number Splitting Attack — Proposal and Analysis of an Experimental Scheme, Advanced Quantum Technologies (2024). DOI: 10.1002/qute.202300437
Feature image credit: Barak Dayan
This article was updated on June 7, 2024 to include a second quote from the study’s lead author, Eliahu Cohen, in the article’s last section.